So, at work we had a lot of customers that were asking for new ipv4’s all of the time, and it’s a little known thing to the mainstream that it is actually possible to configure SSL just fine without the addition of a new IP, or the implementation of SNI (Server Name Indication).
Here is how I configured a basic apache2 server without the need for additional IP’s or SNI. The trick is to use ports. This works for Debian, Ubuntu and also CentOS, RHEL and Fedora but you will want to replace apt-get with yum for the latter 3 distributions.
(for security purposes, I removed the real private and public network IP of my servers to prevent attacks. It does however not affect the clarity of this tutorial providing that you bear in mind you need to replace your load balancer private IP in the apache2 virtualhost configuration. )
1. Step 1, Install apache2 and enable SSL
apt-get update apt-get install apache2 a2enmod ssl service apache2 restart
2. Step 2 Create Self Signed Certificates (optional step), you can use some SSL certificates you purchased instead, place them in /etc/apache2/ssl/your.website.com.crt and /etc/apache2/ssl/yourwebsite.com.key for organisational reasons.
mkdir /etc/apache2/sslmkdir -p /var/www/shop.example.com/htmlopenssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/apache2/ssl/apache.key -out /etc/apache2/ssl/apache.crtThe prompt looks like this; answer the contact and country details, this can generally be anything but be sure to include your FQDN ( fully qualified domain name ) that you want SSL to run with. I will be configured shop.example.com
Country Name (2 letter code) [AU]:US State or Province Name (full name) [Some-State]:New York Locality Name (eg, city) []:New York City Organization Name (eg, company) [Internet Widgits Pty Ltd]:Your Company Organizational Unit Name (eg, section) []:Department of Catz Common Name (e.g. server FQDN or YOUR name) []:shop.example.com Email Address []:[email protected]3. Step 3 Configure Apache2 with your primary IP address using SSL being sure to ensure that you specify an SSLCertificateFile and SSLCertificateKeyFile. You generated the CertficateFile and KeyFile in step 2, but the below directive is an example of how I configured a HTML website for use with SSL
<VirtualHost 134.213.1.1:443> ServerName shop.example.com DocumentRoot /var/www/shop.example.com/html CustomLog /var/www/shop.example.com/access.log combined ErrorLog /var/www/shop.example.com/error.log DirectoryIndex index.html SSLEngine on SSLCertificateFile /etc/apache2/ssl/secure.website.com.crt SSLCertificateKeyFile /etc/apache2/ssl/secure.website.com.key </VirtualHost>
You now have a functioning SSL website with self signed certificate running on a primary IP. If you want to add a load balancer without an additional IP address then keep reading, because that’s the next part.
4. Create a Load Balancer in the Rackspace Control Panel.
Important things to notice here is that.
a) Configure sensible name for load balancer representing TLD I want to host
b) Configure Port 443 for the incoming connections to the Load Balancer
c) Configure Port 543 for the outgoing connections to your cloud server

Once your configuration looks like this you should be almost ready.
5. Configure Apache2 for use with a Rackspace Load Balancer
Previously, in step 3, you configured SSL on apache2 for a single IP address which was publicly accessible. Because the server is now behind a load balancer we need to tell the apache2 webserver to listen on a local private ip address, 10.0.0.1, we also need to tell apache2 webserver to expect connections from the load balancer on port 543. So we need to modify the apache configuration for apache2 to listen on port and to bind to the correct IP now load balancer is sending requests thru the private network instead than to it’s public IP. This is the magic of using a load balancer, you don’t need separate IP’s on the apache2 , the load balancer has an IP already, and you can simply identify the SSL configurations in virtualhosts by binding to ports as opposed to IP’s to provide that isolation necessary for secure SSL. It’s simple to do:
Listen 543
<VirtualHost 10.0.0.1:543>
#ServerName localhost
ServerName shop.example.com
DocumentRoot /var/www/shop.example.com/html
CustomLog /var/www/shop.example.com/access.log combined
ErrorLog /var/www/shop.example.com/error.log
DirectoryIndex index.html
SSLEngine on
SSLCertificateFile /etc/apache2/ssl/shop.example.com.crt
SSLCertificateKeyFile /etc/apache2/ssl/shop.example.com.key
</VirtualHost>
As you can see we added a new IP for the VirtualHost, this is the private IP of the Rackspace Server:
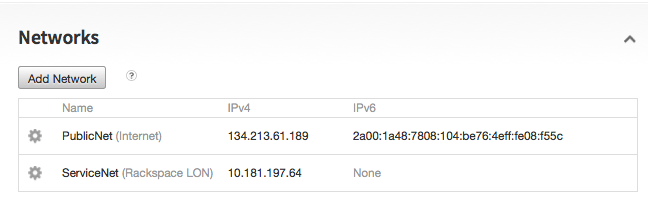
All Rackspace cloud Servers have two networks, a public network IP like we configured earlier as 134.213.1.1. And a private network IP 10.0.0.1 for internal communications between things like the load balancer and this cloud server.
Also you can see we added a Listen 543, this tells Apache2 to listen to connections on this port so that the load balancer can connect to apache2 to send data.
5. Restart apache2 and chmod your directories with the right user and group permissions like you would on any apache2 server
chmod -R www-data:www-data /var/www/shop.example.com/html
service apache2 restart
