After many people popularly requesting to me to document how I configured my Raspberry Pi 2 with retropie to play Arcade Games. Many different consoles are supported. It really is quite extensive. From what I understand, the Operating System is ‘retroarch’ with some modifications, and emulation station, a kind of ‘suite’ of Console and Arcade Emulators of various different kinds.
3do (lr-4do) (EXPERIMENTAL)
Amiga (UAE4ALL2), (UAE4ARM)
Amstrad CPC (CPC4Rpi), (lr-cap32)
Apple II (Linapple)
Atari 2600 (Stella), (lr-stella)
Atari 5200, and Atari 8 bit series: 400, 800, 1200XL, 600XL, 800XL, 130XE, XEGS (Atari800)
Atari 7800 (lr-prosystem)
Atari Jaguar (lr-virtualjaguar) (EXPERIMENTAL)
Atari Lynx (lr-handy)
Atari ST/STE/TT/Falcon (Hatari)
CoCo (XRoar)
Commodore 64 (Vice)
Dragon 32 (XRoar)
Dreamcast (Reicast) (EXPERIMENTAL!)
FinalBurn Alpha (PiFBA), (lr-fba), (lr-fba-next)
Genesis/Megadrive (DGEN), (lr-Genesis-Plus-GX), (lr-picodrive)
Game Gear (Osmose), (lr-Genesis-Plus-GX)
Game Boy (lr-gambatte)
Game Boy Color (lr-gambatte)
Game Boy Advance (gpSP), (lr-gpSP), (lr-vba-next), (lr-mgba)
Intellivision (jzIntv)
Macintosh (BasiliskII)
MAME (AdvanceMAME), (MAME4ALL-Pi), (lr-imame4all), (lr-mame2003), (lr-mame2010)
MasterSystem (lr-Genesis-Plus-GX), (lr-picodrive), (Osmose)
MSX (lr-fmsx), (lr-bluemsx)
Neo Geo (GnGeo-Pi), (PiFBA), (lr-fba), (lr-fba-next)
Neo Geo Pocket (Color) (lr-mednafen-ngp)
Nintendo 64 (Mupen64plus), (lr-mupen64plus)
Nintendo DS (lr-desmume) (EXPERIMENTAL)
Nintendo Entertainment System (lr-fceumm), (lr-nestopia)
PC (DOSBox), (rpix86)
PC Engine/TurboGrafx-16 (lr-mednafen-pce-fast)
Ports
Cave Story (lr-nxengine)
Descent 1 & 2 (DXX-Rebirth) (EXPERIMENTAL)
DOOM (lr-prboom), (ZDOOM)
Duke Nukem 3D (EDuke32)
KODI (EXPERIMENTAL)
Minecraft Pi Edition (EXPERIMENTAL)
OpenTTD (openttd) (EXPERIMENTAL)
OpenTyrian (EXPERIMENTAL)
Quake Series (lr-tyrquake), (ioQuake3)
Super Mario War
SuperTux
Wolfenstein 3D
PlayStation 1 (lr-pcsx-rearmed), (pcsx-rearmed)
PSP (lr-ppsspp), (ppsspp) (EXPERIMENTAL)
ScummVM
Sega 32X (lr-picodrive)
Sega CD (lr-picodrive)
Sega Saturn (lr-yabause) (EXPERIMENTAL!)
Sega SG-1000 (lr-Genesis-Plus-GX)
Super Nintendo Entertainment System (PiSNES), (snes9x-rpi), (lr-armsnes), (lr-catsfc), (lr-pocketsnes), (lr-snes9x-next)
Vectrex (lr-vecx)
Videopac or Odyssey2 (lr-o2em)
Virtual Boy (lr-beetle-vb) (EXPERIMENTAL)
WonderSwan (Color) (lr-mednafen-wswan)
Zmachine (Frotz)
ZX Spectrum (FBZX), (Fuse), (lr-fuse)
Now down to business, actually getting this up and running. Pre-requisites are Rasperry Pi 2 and some power, and a controller or keyboard, that is about it. Oh of course, you need a super microsd card!
Step 1. Download the Retropie Images to your hard disk.
RPI 3.2.1:
http://downloads.petrockblock.com/images/retropie-v3.2.1-rpi2.img.gz
Step 2. Download Win32Disk Imager (this is used to put the image you downloaded above onto the microsd)
http://sourceforge.net/projects/win32diskimager/
Step 3. Open up win32disk imager
It's easy. Make it look a bit like the image below and follow these steps:
Find the retropie-v3.2.1.-rpi2.img.gz file and unzip with winrar, or winzip, or something like 7zip, pkzip, or any uncompressing app should do.
Select that as the 'source image'.
Select the destination (whichever device which is the sdcard in your sdcard reader) , usually something like D:\ , E:\ or F:\, for me it's H:\.

Step 4. Take that fresh microsd card and pop it into the rasperry pi 2. Connect USB power and keyboard, preferably.
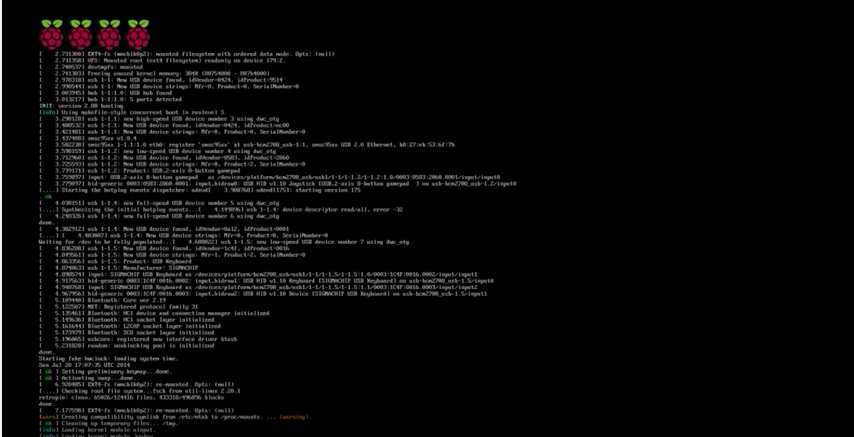
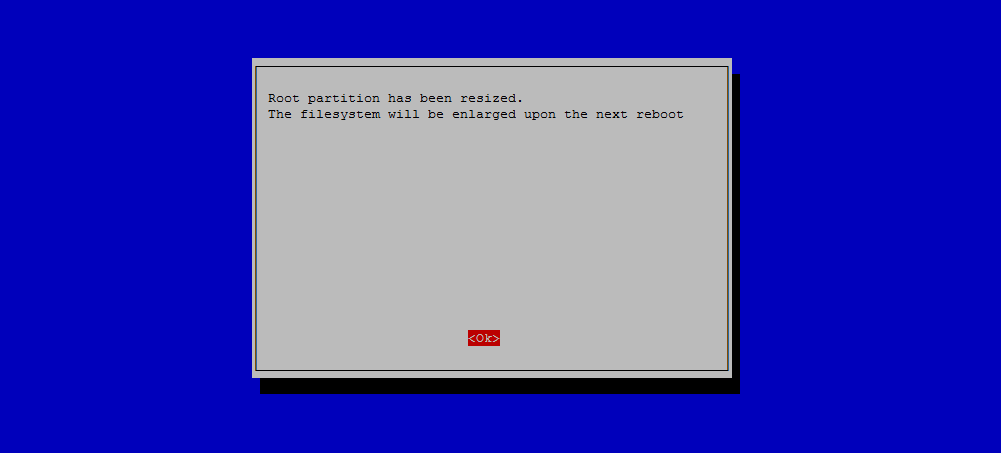
mmm. Tastes good. Like Raspberries. This is pretty much it. Very easy. But what about the ROMS?! arghh??? Yeah, true. The next two steps for that, but first, it makes sense to expand the filesystem. It basically lets you use the full space on the SDCARD, try not to think about it. It’s important , though.
You can press F4 on the keyboard at any time to drop to command prompt and you can type raspi-config yourself to expand the filesystem. But here is to do it from the ‘retropie’ menu selection in emulation station, the GUI that automatically starts with Retropie.

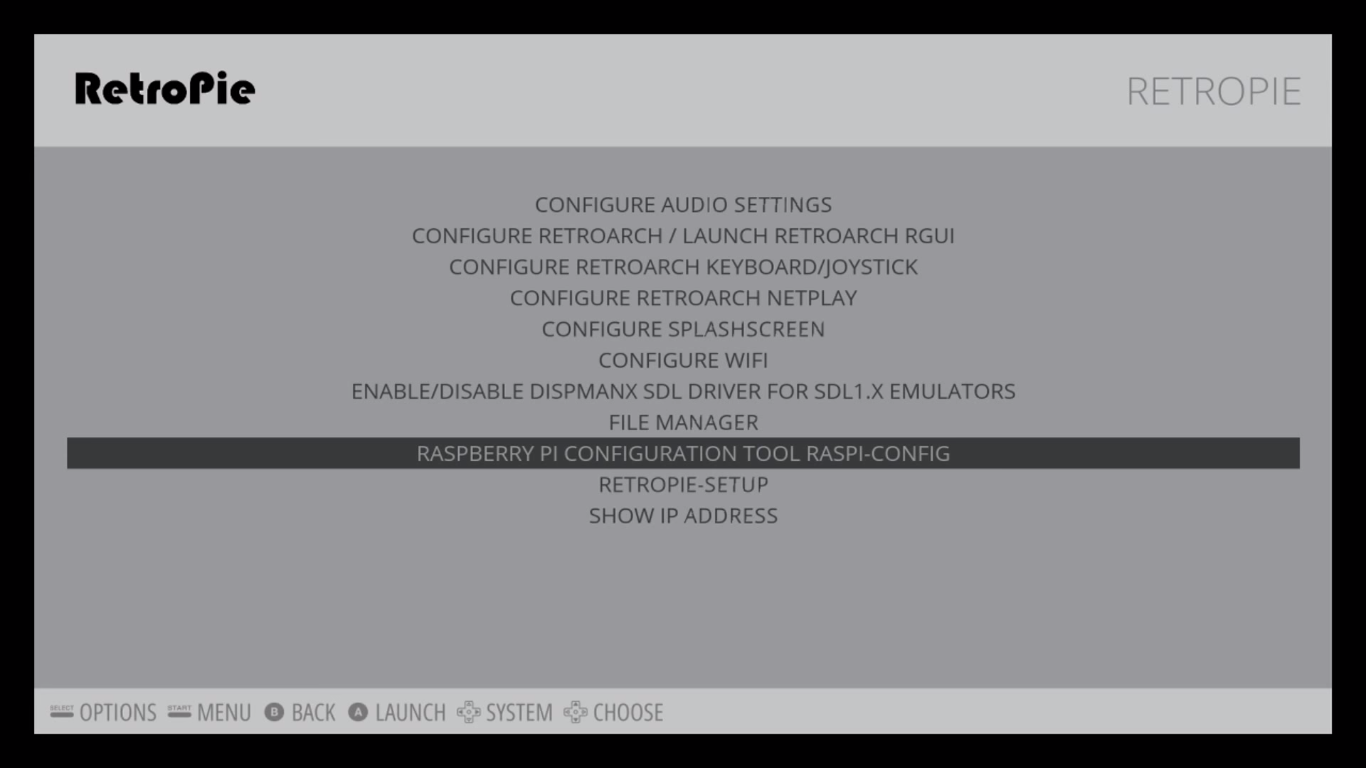
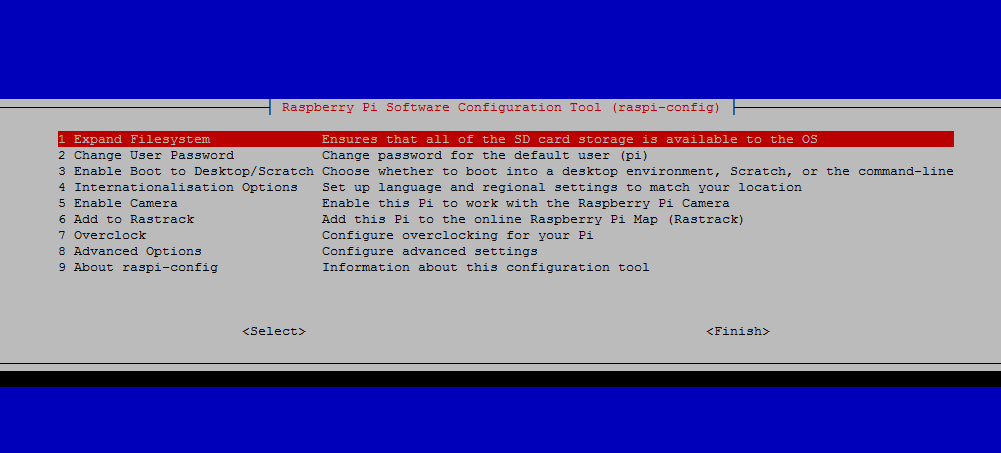
Step 5. Get a generic USB stick, 16GB or 32GB would be ideal, especially if you have a lot of ROMS. Preferably one with an LED on it which shows when it is read/writing. This is handy and you’ll see why later.
Plop the USB stick in your computer, format with FAT32 by right clicking device in windows and selecting ‘FORMAT’.
Create a folder in the highest directory for the USB stick, call the new folder ‘retropie’,
H:\retropie
Plop the USB stick into the retropie, and be patient, wait for the USB stick to flash, and then stop flashing if you have one that flickers LED when its being read/written to
Once the LED on USB stick stops flickering, remove it from the Rasperry pi2, and put it back into your computer. Copy the roms into the relevant folders, i.e. for n64, the n64 folder, for nintendo entertainment system the ‘nes’ folder, for megacd the ‘segacd’ folder, and for genesis the genesis/megadrive folder. You get the idea, it’s really simple. Once you’ve finished copying them to USB stick, take the USB stick out of your pc again.
Place the USB stick in the retropie, it has a service that checks for any changes on the USB stick, and it automatically rsyncs (synchronises the files on the USB stick with it’s sd card. If you were awesome and used an USB stick that flickers LED when writing/reading, wait for it to stop flickering before removing from rpi!
Now restart the thing (and this might not even be necessary), and then the emulation station will show the icons for the devices you’ve added roms for (don’t panic if you can’t see some emulators, if you didn’t put roms in the folder, then it won’t show up, think about it , this makes sense for almost 100 different emulators shipped, not to see the ones you have no roms for! It got me for a little while until I put that together.
Some really super duper important caveats:
Segacd requires copyrighted BIOS uploaded to the /opt/rpi/BIOS folder, or some such. Will document this more later.